To read more about The Impact of a Strategic IT Service Provider, click the link below
Read MoreTo read more about How Cybercriminals Use AI to Power Their Attacks, click the link below
Read MoreTo read more about How to Build a Security-First Culture That Empowers Your Hybrid Workforce in Upstate NY and Beyond, click the link below
Read MoreTo read more about Enhance Small Business Cybersecurity in Albany NY: Expert Tips, click the link below
Read MoreGroff meets Kevin Brown, Motivational Speaker & Author
Read MoreWhat did it take to be one of the 2023 Best Places to Work? Perks and benefits certainly help. But more than anything else, this year’s winners developed cultures...
Read MoreHere are the three of the most prevalent ransomware myths that you'll need to know in order to fully protect your business.
Read MoreHelp protect your business by implementing these best defense practices against ransomware!
Read MoreIf you want your organization to invest in a policy and receive a payout in the event of a cyber incident, you can’t fall for these cyber insurance myths!
Read MoreCyber insurance is a must-have for any business that wants to protect itself from cybercrime and online security threats. Learn how you can stay protected!
Read MoreTake your cybersecurity to the next level by following along with these simple steps. Help protect your business and your future.
Read MoreFollow along with these simple tips in order to help your company further strengthen its cybersecurity.
Read MoreCyber Incidents can happen at anytime, which means having a balance between proactive and reactive approaches are key within any business.
Read MoreEffective processes and technologies that support employees and personal goals can help your organization become and remain sustainable. Here's how!
Read MoreEvery successful business is built upon strong human relationships and trust. Here are four important steps that will help increase your overall trust.
Read MoreHow do you know which IT service provider is the right fit for your business? Here are some suggestions to help you decide.
Read MoreRemote work has now become normalized within our culture, so implementing the best security practices is a must. Here are some of the best practices to start with.
Read MoreHere are some of the many benefits of having a managed IT service provider.
Read MoreThe important responsibility that we all must share, in order to get the job done right. Here's what you need to know.
Read MoreLearning about the dark web is one thing, but implementing a strategy that can help prevent future cyber attacks is another. Click here to learn more.
Read MoreThe most vital component within every company is simply moving beyond single-layered passwords. Here's how you can further protect your company's security.
Read MoreImplementing the right security training could help eliminate any weak spots that are targeted by security threats and here's why!
Read MorePromoting confidence in your employees and the steps they take in order to mitigate cybercriminals will be invaluable to your business.
Read MoreFollow along with these seven helpful tips in order to further protect yourself and your company from future phishing emails.
Read MoreImplementing a cyber readiness plan into your routine could be the answer to your company's security concerns.
Read MoreLet's take a closer look at your password strength and vulnerability. Do you think your password can pass the test?
Read MoreHave your credentials become compromised? Follow these helpful steps in order to further secure your privacy in the future.
Read MoreGroff Networks was involved in one of the largest and most comprehensive ranking surveys in the IT industry: The MSP 501 Channel Futures. Here's how we ranked!
Read MoreHelp your company from being another statistic and follow this guideline to help better protect your company from fraudulent attacks.
Read MoreIn this episode of Teco Tuesday, we discuss what the ideal economic model for small business should really look like.
Read MoreIn this episode of Teco Tuesday, we discuss some Anti-Hacking Tips that could save you and your company from a serious security attack.
Read MoreYou should always think twice before posting your personal information on any media platform and here's why...
Read MoreA new year means new malware trends. Learn how you can avoid these ongoing hackers trends.
Read MoreHere are a few tips for owners and hiring managers to help keep high levels of productivity and efficiency in the workplace.
Read MoreGroff Networks has participated in the 13th Annual Channel Futures MSP 501 Rankings and we are proud to announce the results. Click here to see how we ranked!
Read MoreWhat is BEC and why is it important for all small businesses to know?
Read MoreLearn how to save yourself, your employees and your business from becoming phish bate by following these simple tips.
Read MoreIn this episode of Tech Tuesday, Lauren Groff talks about what the Network Administrator role entails at Groff Networks.
Read MoreAre you prepared for the inevitable upgrade to Windows 10? Here’s why you should make the switch to the new Windows operating system.
Read MoreHere are the four big mistakes that small businesses tend to make and how you can easily avoid them in the future.
Read MoreKnowing how to avoid fraudulent sites can instantly help protect your personal information. Here are a few suggestions on how to go about doing so.
Read MoreOur mission is to impact the world in a positive way through technology success. We are here to help, so let us help you!
Read MoreHave you ever gotten an email from your boss or client that just doesn’t feel right? Trust your gut and think before you click on that suspicious email.
Read MoreLauren Groff doesn’t mind talking about his competitive advantage, or giving away his industries secrets. Well, why not?
Read MoreThe Japanese government is attempting to hack into their own citizens' devices. Now what?
Read MoreThese are the three big cybersecurity tips that you and your company are not gonna want to miss!
Read MoreIn this episode of Tech Tuesday, Lauren Groff is joined by Peter Briden of TruMethods. Peter shares his extensive knowledge and wisdom with you.
Read MoreWhat does it actually mean when your email is hacked and what are the different ways you can avoid these ruthless hackers? Click to learn more.
Read MoreInterning might just be one of the most crucial moves you can make as a young adult. Learn why being an intern is an important step towards any career.
Read MoreIn other words, make sure that your IT firm is fully aware of your aging technology and that they always have a plan to reduce your risk(s).
Read MoreTake precaution when it comes to new connective devices. Remember, the more connected devices you have, the more treats you are leaving out for hackers to snack on.
Read MoreIn this episode of Tech Tuesday, Lauren Groff discusses the importances of getting what you deserve out of your IT support.
Read MoreNew laptop? Then stay protected by following these simple steps that could save you from a potential security threat.
Read MoreIn this episode of Tech Tuesday, Lauren Groff talks about the necessary steps in order to achieve technology success.
Read MoreIn this episode of Tech Tuesday, Lauren Groff is joined by Lauren from TruMethods to discuss the importance of cybersecurity education.
Read MoreThe well-known Mariott admits to purchasing an already hacked hotel and here's what happened!
Read MoreIn this episode of Tech Tuesday, Lauren Groff is joined by Gary Pica of TruMethods to discuss the importance of IT being implemented into your business strategy.
Read MoreHere is the real question; why would any business still use a server?
Read MoreDid you know that unsubscribing from an email doesn't prevent you from receiving other spam emails, it actually opens up the door further. Here is why!
Read MoreIn this episode of Tech Tuesday, Lauren Groff is joined by Bob Penland of TruMethods to discuss the importances of strategic direction in IT.
Read MoreIn this episode of Tech Tuesday, Lauren Groff discusses the importances of going into great detail when it comes to topics based around IT.
Read MoreThis is a huge thank you to all of our clients, users and our staff for making IT great again. We appreciate you!
Read MoreIn this episode of Tech Tuesday, Groff discusses how much money you should be spending when it comes to a businesses IT.
Read MoreIn this episode of Tech Tuesday, Lauren Groff discusses the most important metric for you to know about your businesses IT.
Read MoreYou might as well replace that “s” in cybersecurity with a $ based on what we’ve seen out there. Here's why!
Read MoreCheck out these 5 tips to protect your business without breaking the bank. You won't want to skip over this!
Read MoreGroff NetWorks has seen a spike in old yet effective phishing methods, but with a new technical twist. Here's what you need to know!
Read MoreTo read more about Critical Security Controls, click the link below
Read MoreTo read more about Cybersecurity Training Tips, click the link below
Read MoreTo read more about Business Is a Teenager…, click the link below
Read MoreTo read more about Hackers Are Targeting Children, click the link below
Read MoreTo read more about Phishing Surpasses Malware Attacks, click the link below
Read MoreTo read more about Encrypted Email Signs, click the link below
Read MoreTo read more about Core Data Security, click the link below
Read MoreTo read more about Tech Support Scams On The Rise, click the link below
Read MoreTo read more about Mobile Devices in the Workplace, click the link below
Read MoreTo read more about Implementing Cybersecurity, click the link below
Read MoreTo read more about The Intel Crisis: Where We Stand Now, click the link below
Read MoreTo read more about How to Build a Great IT Strategy, click the link below
Read MoreTo read more about The Future of Security, click the link below
Read MoreTo read more about Confessions of a ‘Job Creator’, click the link below
Read MoreTo read more about iPhone X vs. Pixel 2 XL, click the link below
Read MoreTo read more about Master These Critical Security Controls, click the link below
Read MoreTo read more about Equifax: The Road To Recovery, click the link below
Read MoreTo read more about Make Sure your Children are Safe Online, click the link below
Read MoreTo read more about Better Your Life With Home Automation, click the link below
Read MoreTo read more about New NYSDFS Policies, click the link below
Read MoreTo read more about Equifax Falls Victim To Worst Hacks, click the link below
Read MoreTo read more about That Scary ‘A’ Word, click the link below
Read MoreTo read more about Creating Strong Passwords, click the link below
Read MoreTo read more about Server Swap Didn’t Go According to Plan?, click the link below
Read MoreTo read more about Groff NetWorks Ranked GLOBALLY, click the link below
Read MoreTo read more about Smishing; Your Newest Security Threat, click the link below
Read MoreTo read more about IT Workers: Getting Breaks They Deserve, click the link below
Read MoreTo read more about Storm Season: Dangerous for Your Business, click the link below
Read MoreTo read more about Protect Yourself From Ransomware, click the link below
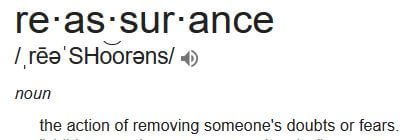
Read MoreTo read more about Ransomware Attacks: Fearful or Reassured?, click the link below
Read MoreTo read more about 12 Years Ago: Today, click the link below
Read MoreTo read more about IT for Small Business, click the link below
Read MoreTo read more about Slow Printers? Here’s Why, click the link below
Read MoreTo read more about The Dangers Of Computer Systems, click the link below
Read MoreIn business today the choice of a technology advisor can be a critical success factor in this article you’ll learn how to make the right choice. Maintaining your...
Read MoreTo read more about ONE CLICK AWAY FROM RANSOMWARE, click the link below
Read MoreTo read more about Strategies For Picking New Computers, click the link below
Read MoreTo read more about When IT Makes You Mad, click the link below
Read MoreTo read more about How to Protect a VoIP System, click the link below
Read MoreTo read more about Capture a screenshot in an iPad, click the link below
Read MoreTo read more about Turn off Flash in your Browser on Android, click the link below
Read MoreTo read more about Use Your Android Phone Like a USB Key, click the link below
Read MoreTo read more about Hide Windows Desktop Gadgets Quickly, click the link below
Read MoreTo read more about Unsend Emails Sent Using Gmail, click the link below
Read MoreTo read more about Remove the Image Background in Bing, click the link below
Read MoreTo read more about Split Keyboard on an iPad, click the link below
Read MoreTo read more about Converting Currencies Using Google, click the link below
Read MoreTo read more about Set which Desktop Applications will Open on Mac OSX Lion, click the link below
Read MoreTo read more about Set Switch Preference to Orientation Lock or Mute on Your iPad, click the link below
Read MoreTo read more about Changing the Default Apps on your Android Device, click the link below
Read MoreTo read more about Dial Phone Numbers in Safari on an iPhone, click the link below
Read MoreTo read more about Disable Tab Previews of Internet Explorer in Windows 7, click the link below
Read MoreTo read more about Change the AutoRecover Interval in Microsoft Office 2007/2010, click the link below
Read MoreTo read more about Lock Access to Your Windows Desktop Quickly, click the link below
Read MoreTo read more about Trigger Animation On Click of an Object in Microsoft PowerPoint 2010, click the link below
Read MoreTo read more about Rename Files Quickly in Windows 7, click the link below
Read MoreTo read more about Search within a Site Easily Using Google Chrome, click the link below
Read MoreTo read more about Change the Speed, Look, and Behavior of Your Mouse Pointer Easily in Windows, click the link below
Read MoreEmail plays a big role in the way people do business. Whether you work from a fixed location at an office desk or from a mobile device on...
Read MoreTo read more about Guide to Changing the Screen Resolution of Your Monitor, click the link below
Read MoreSomeone, somewhere could be talking about you or your company, and — depending on what’s being said — it can be either helpful or damaging to you or...
Read MoreTo read more about Forget to Include an Attachment in Outlook? Get a Reminder!, click the link below
Read MoreFor companies interested in trying out cloud-based services, email maybe something worth trying. Here’s a breakdown of two options from two industry giants that may be worth considering....
Read MoreSmaller businesses usually face the difficulty of having their voices heard in the market today. While traditional marketing and advertising methods cost a lot more than many of...
Read MoreTo read more about Display all available action options in the Windows Control Panel, click the link below
Read MorePart of establishing a proper security cordon around your business data is having the right hardware – like a router/firewall – to get the job done, and done...
Read MoreWith so many smartphones out on the market these days, many would-be users find it difficult to choose which one works best for them. There is no right...
Read MoreTo read more about Color Code Messages Addressed Only to You in Outlook, click the link below
Read MoreAs systems and market demands continue to require better productivity and efficiency, it only follows that the software that businesses use also needs to upgrade sooner or later....
Read MoreCheck out these top ten reasons why you should consider switching to VoIP phones for your business. Voice-over-Internet Protocol (VoIP) is basically technology that allows you to make...
Read MoreTo read more about Integrated View of Google Services in Firefox, click the link below
Read MoreThere is no doubt that the iPad has changed the computing market, specifically the tablet computing segment. With nearly 25 million sold so far, with 9.25 million of...
Read MoreTo read more about Save Files Directly to the Cloud, click the link below
Read MoreDo you ever wish you could save files you find online directly to a cloud storage service provider? With this handy new free tool called Cloud Save you...
Read MoreWhen presenting in front of an audience, sometimes it’s necessary to pause your PowerPoint slideshow for a few minutes to highlight a point, answer audience questions, or to...
Read MoreWhile Microsoft’s Internet Explorer continues to enjoy a wide audience – businesses included – a new flaw has been discovered in the browser. Called “cookiejacking”, the flaw allows...
Read MoreSometimes you need to find out your IP address for networking, troubleshooting, gaming, or tech support purposes. There are two IP addresses you may need to consider —...
Read MoreKeeping your IT system safe is more than just getting the right security software – it also entails training your employees to become more responsible users and making...
Read MoreIf you’re one of those people who believe that Macs are impervious to virus attacks, it may be time to rethink that belief: A new threat to Mac...
Read MoreWant to pay for merchandise without whipping out a credit card? Google makes this possible with an electronic internet-based service called Google Wallet. You simply swipe your smartphone...
Read MoreHave you ever struggled with fitting the contents of your Excel spreadsheet on one page? There are several ways to get around this, one of which is to...
Read MoreIdentity theft is one of the most common cyber-crimes these days, as more and more people become dependent on the internet for many of their needs. Fortunately, following...
Read MoreWant to change the default download location for Mozilla Firefox? Perhaps you want to have it default to your desktop, or a special folder on your hard drive?...
Read MoreOne of the most dangerous yet common mistakes business owners make is assuming “it will never happen to me”. However, there are only two types of people: those...
Read MoreOn some computers with really large drives, the Recycle Bin’s default size setting (10% of your hard drive space) can be too much and may be an inefficient...
Read MoreCost savings are usually important to small businesses even in the best of times. New technology solutions may be necessary for survival and growth, however — and they...
Read MoreMany small and medium-sized businesses have the misconception that they are safe from cyber-attacks because of the lesser profits cyber-thieves can make from them. But recent studies show...
Read MoreMany users download Adobe Acrobat Reader to open PDF Documents, but it can be slow to start up and load a file. However, you can use Chrome as...
Read MoreCost savings are usually important to small businesses even in the best of times. New technology solutions may be necessary for survival and growth, however — and they...
Read MorePublic Wi-Fi is all well and good, but its very nature makes it easy to exploit and allow hackers access into your system – unless you have the...
Read MoreWhile the cloud can be a good place to store data and backups, you need to make sure you can quickly get it when you need it. Restoring...
Read MoreWhen Windows 7 was released, it introduced a new feature called Snap — which allows users to easily resize windows when they are dragged to the edges of...
Read MoreCost savings are usually important to small businesses even in the best of times. New technology solutions may be necessary for survival and growth, however—and they may not...
Read MoreA recent attack by cyber-criminals has highlighted the need for many SMBs to re-evaluate the security protocols between themselves and their bank. Hackers exploit weaknesses in such systems,...
Read MoreAre you investing in IT to win — or just to keep up? Many, if not most, companies use IT as a tool, and in doing so they...
Read MoreGoogle’s Chrome browser has special commands that can show you basic browser settings and info from within the browser’s main window. This can be helpful since it presents...
Read MoreCost savings are always important to small businesses — but that doesn’t mean you should skimp on technology. New technology may be necessary for the survival and growth...
Read MoreWe are seeing Macs and PCs together in more and more offices. Here are some tips to make sure these devices can get along with each other —...
Read MoreOne of the world’s leading email service providers, Epsilon, found itself the victim of a phishing attack that saw a significant amount of data lost to cyber-thieves. It’s...
Read MoreGoogle is making its searches more effective through the introduction of Google +1, an experimental program that allows users to recommend websites by pressing a +1 icon that...
Read MoreThere are times when you might want to open multiple instances of the same software program quickly, such as when you need to work on multiple documents in...
Read MoreA lot of businesses make it a habit to back up their data, and leave it at that. But many do not realize that there is another half...
Read MoreDual or multiple screens may seem excessive for some, but in truth it might just be the thing that helps you boost productivity and efficiency in the workplace....
Read MoreInstead of copying files to multiple locations in your hard drive to make sure you can find it easily, consider using shortcuts instead. Shortcuts are simply links to...
Read MoreA recent study by IT security firm Symantec shows that at least half of SMBs lack the proper security for their systems, which puts both them and their...
Read MoreThe growth of technology in the business environment has been a boon, but it also gives departing employees many methods of taking data with them. In the past,...
Read MoreDid you know that typing “about:” plus another word in Firefox will allow you to view special configuration information of the browser — some of which you can...
Read MoreWe often send out highly sensitive, if not confidential, information through our email accounts such as banking information, passwords, pictures, and more. But how many of us actually...
Read MoreThe 8.9 magnitude earthquake off the eastern coast of Japan was not a local event; it triggered a tsunami warning for Southern California, impacting many American companies —...
Read MoreMicrosoft has made business operations much simpler and more accessible through the new Windows Small Business Server 2011. Packed with enhanced features and improvements, it is a must...
Read MoreIf you share your computer with other users or manage the computers in your home or office, there are times when you may want to restrict users from...
Read MoreBusinesses are constantly looking for ways to maximize productivity and minimize costs without compromising the quality of their output. One of the simplest ways you can go about...
Read MoreDo you have a Gmail account but prefer using Outlook to access your email? You can configure your Gmail to behave like a normal mailbox so that you...
Read MoreWith hackers and electronic thieves constantly on the lookout for the latest exploits and security breaches they can take advantage of, it is comforting to know that there...
Read MoreAdding a shortcut to the Recycle Bin is easy if you know how to edit your system registry. Here’s how: First go to the Windows Start Menu and...
Read MoreTwitter is now five years old, and the social networking website famous for its 140-character “tweets” continues to make waves as both a powerful social networking and social...
Read MoreMajor sporting events can be a cause for concern for business owners and managers as employees shift their attention from work to keeping themselves updated through video streaming...
Read MoreWould you like to customize the Windows 7 Logon Screen and use your own wallpaper image? There are actually several ways to do this. The first method involves...
Read MoreMore and more people are demanding that business establishments they visit provide free Wi-Fi. Setting up the hotspot network yourself might seem to be a good idea, but...
Read MoreWhen you installed MS Office 2007 or 2010, you had the choice of installing the entire suite or picking and choosing which apps you wanted. If you now...
Read MoreSkype, together with its partners Panasonic and Samsung, has developed the first generation of Skype-enabled TVs that allow you to call and receive video calls from anyone who...
Read MoreHave you ever clicked “Never Remember” for a password, only to decide later that you do want Firefox to remember it? Here’s how you can get Firefox to...
Read MoreSoftphones make communication much easier by using an internet connection to make a call. But for businesses, PABX softphones offer much more secure communication for your day-to-day operations....
Read MoreWindows 7 offers location-specific Aero themes based on the language and location you pick during installation. But did you know you can access other hidden themes from different...
Read MoreProfessional service providers such as attorneys, accountants, and doctors no longer fall within the definition of a creditor under the Red Flag Rule. The Federal Trade Commission’s (FTC)...
Read MoreWhy are companies rolling out their own private networks? Find out what private networks are and how you can benefit. The world is flat. That is if you...
Read MoreMozilla Firefox too slow? Here’s a tip for speeding up Firefox by moving cache memory to RAM. Read more .
Read MoreIn a society where more and more people are relying on smartphones to stay connected, internet marketing strategies must now incorporate smartphones into their approach. One way to...
Read MoreMacs are famous for a lot of things – some true, some false. Unfortunately, being virus or malware-proof is one of the myths about the Mac that you...
Read MoreWith the many choices today in smartphone platforms, one new contender stands out from the pack – Windows Phone 7, Microsoft’s new smartphone OS. A growing tech trend...
Read MoreWish you could access the run command in Windows 7 more easily? Now you can. Read more .
Read MoreWhat makes a phishing message tick? Identify phishing messages from the get go and stop yourself from becoming another statistic. Online oracle Wikipedia defines phishing as: “the criminally...
Read MoreDo you send lots of e-mails every day? If so, this tip is for you. Save time by creating a shortcut on your desktop that will open a...
Read MoreWith multiple gadgets being used by a single person, one is bound get misplaced occasionally – or worse, stolen. This can be very annoying and even devastating, but...
Read MoreNew vulnerability can potentially allow hackers to remotely control PCs A new vulnerability found in Microsoft’s Windows operating system can potentially open up your PC to remote attackers....
Read MoreFirefox 3.6 has yet another secret feature that could significantly improve your web browsing on Windows: scroll acceleration. Read more .
Read MoreYour email account contains much of your private information. If this vital info gets into the hands of email hackers they can do a lot of harm to...
Read MoreUSB flash drives are very handy for storing backups, personal documents, music, pictures, portable applications, and more. In fact, they’re so convenient that we dump information onto them...
Read MoreTired of slow printing? You can take action speed up the processing time of your printer, as well as the printing speed itself. These tips are easy to...
Read MoreScammers are getting sneakier these days, using increasingly underhanded tactics to bait unsuspecting victims. One new scam involves asking for a “registration fee” for getting better visibility on...
Read MoreWhen you acquire equipment for your businesses, you can deduct the entire cost in a single year, thanks to a tax break that’s been extended through the end...
Read MoreReadyBoost can speed up your computer by using storage space on most USB flash drives and flash memory cards. Read more.
Read MorePlug-in USB devices, such as thumb drives, USB storage hard drives, are a very popular method of transferring digital files. However, they have also lately become a hacker’s...
Read MoreWith the growth of social networking, it is becoming increasingly difficult to separate business connections with personal connections. November 17, 2010 was declared by Jimmy Kimmel during his...
Read MoreA new year means a fresh start (or a compulsive desire to stay organized). Why not start today? Here are 5 folders we’ve identified on your PC or...
Read MoreSecurity firm Dasient warns users against the rising number of malware-infected websites. Dasient , a company specializing in combating malware on websites, has released a new report claiming...
Read MoreThe Recycle Bin’s default size is equivalent to 10 percent of the drive size. But if you delete a larger size file accidentally, you might need it to...
Read MoreThe DriveSafe.ly by iSpeech.Org and the Text’nDrive app for Blackberry or iPhone are just two of the latest hands-free apps on the market. These apps rely on text-to-speech...
Read MoreMost people associate pop-ups with annoying advertisements that must be closed to continue reading the web page underneath. However, there are times when you need pop-ups to use...
Read MoreThe federal government’s Red Flag Rule requires all businesses that are potential identity theft targets develop plans to spot red flags and prevent theft. How can you comply?...
Read MoreWhile many companies think the federal Red Flag Rule applies only financial institutions, if you invoice customers for your goods or services, it applies to you, too. Regulations...
Read MoreTo comply with the federal government’s Red Flag Rule, you’ll need to have a written policy that specifically addresses how you will prevent and handle identity theft —...
Read MoreTired of having Excel convert what you type into active hyperlinks? You can make it stop. Read more.
Read MoreUsing shared Wi-Fi networks can be really convenient, but it is not without risks of its own. These days, more and more people are on the go, and...
Read MoreTwitter is arguably the most popular and widely used microblogging platform on Internet today. Though each post is limited to only 140 characters, there are various Twitter applications...
Read MoreSometimes websites use fonts that are too small or otherwise difficult to read. Learn how to set up Firefox to display all webpages with a specific font and...
Read MoreMalicious cyber thieves might be scaring you into buying and downloading software that may harm your computer. Security firm McAfee has published a report early in the year...
Read MoreSorting lists of names by last name is easy if they are listed in a LAST, FIRST order. But what if the names are in FIRST LAST order?...
Read MoreIf success is what you aspire to, you need to know what to do when unexpected events cause harm or hassle to your business. You need to be...
Read MoreHere are some free online tools that can help you modify PDF files. What’s even better is they don’t require downloads or installation. The only requirement is an...
Read MoreA Smartphone is lightweight and portable, making it very prone to accidental drops. Not only do you risk damaging the phone itself, you also risk losing valuable data...
Read MoreCreate easy-to-read and type Internet addresses from the long addresses often found on popular sites such as Amazon, eBay, and MapQuest by using online services that shrink the...
Read MoreStudies show that among US companies alone, 30 billion paper documents are copied or printed every year. The associated cost for each document is estimated at $6.50. Five...
Read MorePeace of mind, security, and superior IT are now made available not just for huge enterprises, but for small to medium-sized businesses as well. Using Managed Services, you...
Read MoreWhen you come across a web page you’d like to share, these simple steps allow you to easily send a link to a friend. Read more.
Read MoreNew research from risk consultancy firm highlights risk from data theft committed by employees. A poll of over 800 senior executives around the world showed that companies for...
Read MoreIf you use Web sites to share your documents, movies, pictures, and music files, you probably know what it means to have to convert files. Good thing there...
Read MoreDisasters of all kinds could inevitably hit your business at any time. Therefore, in addition to having a backup plan, you should also create and implement a disaster...
Read MoreThere’s a boom in geolocation platforms these days, and experts are seeing vast potential in the way geolocation can help small and medium sized businesses put themselves on...
Read MoreIf you spend your day replying to e-mail in Microsoft Outlook, you may find yourself with a stack of open message windows all over your screen by lunchtime....
Read MoreAlmost every activity involves the use of technology, and almost everyone uses the internet. So, it’s only logical that if you want to go into business and be...
Read MoreThe most commonly used feature in Internet browsers is the Back button, and many users click it several times to get where they want to be. However, all...
Read MoreWhy risk the chance of infection and sickness when you can simply take a few minutes each day to disinfect and clean your workspace? It might be terribly...
Read MoreStyles are a powerful feature of Word that help you easily define the way your text should appear. This tip explains how you can define styles or modify...
Read MoreIf you are running a company or a business of your own, you might be asking yourself, “Do I need Managed Services? Is it really worth it considering...
Read MoreIn Office 2010, the locations of some features are different, and if you’ve recently upgraded you might be wondering where you can add signatures to your emails. Here...
Read MoreMost backup solutions available these days certainly do a good job of backing up your data. However, all backup solutions are not the same, and careful assessment is...
Read MoreStart Menu Search is one of the best features in modern Windows versions, but in Windows 7, it can only be used to search for programs and files...
Read MoreBeware! Someone maybe stealing money from you where you least expect it – your bank! According to the US Federal Bureau of Investigation, online criminals have been getting...
Read MoreAmong a host of power management options available in Windows 7, sleep mode is a convenient way to save power and reduce wear and tear on your computer’s...
Read MoreIn the wrong hands, a stolen laptop can compromise your personal security and the security of your business, not to mention the actual loss of the data. This...
Read MoreThese days, printers have become more than just, well, printers. There are many features and factors to consider in your purchase to make sure the printer you buy...
Read MoreThe Windows Disk Cleanup Wizard will delete your temporary files, but only if they are over a week old. Here is a tip that shows you how to...
Read MoreOne of the more subtle ways hackers use to get malware into your system is through programs that are not up-to-date. This is why it is essential that...
Read MoreSome companies have suffered significant data loss because they discovered the errors too late. Put a Business Continuity Plan in place before you experience a major data loss...
Read MoreFinding delicate control with your optical mouse difficult? Does the arrow pointer keep jumping all over the place? Well, here’s a tip that will help. Read more.
Read MoreIt’s common knowledge these days that social networking websites such as the hugely popular Twitter can be used not only as an online socializing medium, but also as...
Read MoreYou may know how to add multiple files to one zip file, but do you know how create individual zip archives for each file automatically? Read more.
Read MoreYour passwords hold the keys to most – if not all – of your online presence, so keeping them secure is paramount. In the same way that keys...
Read MoreDocumentation and assessment of your IT needs might expose the fact that your IT environment is not as efficient as you thought it would be. This may explain...
Read MoreWhen your computer keyboard starts looking dirty, yellowish, or some keys are not working properly, it may be time to learn how to clean it properly. Read more....
Read MoreLosing a smartphone these days means a lot more than just losing the hardware - it can spell a potentially dangerous threat to your business if the wrong...
Read MoreThe performance of a Wi-Fi home network greatly depends on signal strength of the wireless router or wireless access point. To position your wireless equipment for optimal network...
Read MoreClear Cloud is a safe, effective, and simple way to check your browsing habits and keep your computer clean. It’s a simple, straightforward approach to getting better security...
Read MoreMicrosoft sales for Windows XP ceased on October 22, 2010, and support for the old OS will continue only until 2014. If you’ve been using Microsoft XP for...
Read MoreMicrosoft Word and Adobe Reader are probably the most used document editing / viewing applications out there, and documents and PDF files can be used to introduce viruses...
Read MoreMore entrepreneurs these days are using Managed Services for their businesses. Why? Because it’s a good investment that’s sure to help increase a company’s revenue. These days businesses...
Read MoreUsing your Bluetooth-enabled cell phone as a modem for Internet access on your laptop is great in a pinch when there’s no Wi-Fi service available or your regular...
Read MoreJust when we thought we’ve seen it all in the social networking scene, along comes Foursquare, a new social networking app that brings things closer to home -...
Read MoreSD cards can be tricky little gadgets. They sit in our cameras and cell phones, just waiting for us to take the picture of a lifetime. . .at...
Read MoreRefilled ink cartridges may seem to be a cheaper alternative, but careful analysis will show that it actually costs more. Throughout recent months, we’ve seen more and more...
Read MoreYour small business can benefit from tools that track location and position GPS has lately become a near ubiquitous feature in many mobile devices such as car accessories...
Read MoreIf you have ever asked how to change the default background color of the Calendar in Outlook 2007, read on. Read more .
Read MoreOne technique scammers use to bully users into downloading malware is to launch repeated popup attacks prompting users to download their “antivirus” solution. It’s important to stay safe...
Read MoreIf your PDF prints larger or smaller than you want, use Page Scaling to print at the size you’d prefer. Use Tiling to print banners and other large...
Read MoreErratic by nature, disasters (natural or man-made) can happen anywhere at any time, and often with little or no warning at all. Planning ahead is imperative to ensure...
Read MoreAs the social networking phenomenon continues to grow, not only for personal use but for business purposes as well, business email staple MS Outlook now allows for integration...
Read MoreYou can shut down, restart or log off from Windows 7 or Vista in a few quick steps - without going through the Start Menu or using any...
Read MoreThe United States Homeland Security Department’s National Cyber Security Awareness Campaign Challenge was a huge success, with more than 80 security proposals submitted with the goal of increasing...
Read MoreCRM service providers are beginning to realize the value of social networking and are beginning to integrate similar features into their services. With the popularity of social networking...
Read MoreWhen you find yourself performing a task or series of tasks repeatedly Excel spreadsheets, save time by creating a macro to do the work for you. Read more...
Read MoreVoIP is now within reach for everyone - including small businesses. The same network that handles the flow of data such as web access and email can also...
Read MoreJavaScript is a very popular programming language used in many websites, making your web experience more dynamic and interactive. However, hackers can exploit JavaScript and use it to...
Read MoreSeveral printing options in PowerPoint 2007 let you print slides, speaker notes, presentation outline, and audience handouts. Here are tips on how to use them. Read more.
Read MoreUtilizing IT Managed Services allows entrepreneurs to concentrate on their company’s core competencies, resulting in an increase in productivity which translates to increased revenue. The term Managed Services...
Read MoreIf you work while traveling, you can always use a longer battery life. It makes little sense to lug your laptop around if it’s constantly out of power....
Read MoreInternal social networks help when you need to cascade and disseminate information within the company, but you also need the right policies and management to use these networks...
Read MoreA new threat to computer security has been discovered in which tab browsing vulnerabilities are exploited to fool users into divulging passwords and other sensitive information. Dubbed as...
Read MoreSince paper is relatively inexpensive, especially when compared to the price of ink, you may think more about conserving ink. But conserving paper too is great for the...
Read MoreSecurity firm Symantec has uncovered a scheme to extort website owners for money or face the possibility of a DDoS attack. Security firm Symantec recently uncovered a scheme...
Read MoreSkype, Tokbox, and Oovoo are three online video conferencing services that have recently targeted business enterprises with business-friendly features. Many businesses these days are realizing the value of...
Read MoreThe mouse is a primary way of interacting with the computer, so smooth and responsive functioning is a must. Here are some tips for trouble-free mousing. Read more...
Read MoreCampaign to trick users into installing fake antivirus software gaining ground. Beware: a massive email campaign is underway to trick users into opening an HTML file attachment that...
Read MoreData is important to any business, and losing it can spell disaster, which is why it is important to always have backups of your files and information. Let’s...
Read MoreWhen saving a file in Windows 7 you can select a library to save it in – but because libraries aren’t real locations, the file is stored to...
Read MoreGrowth of mobile fueling increased interest in mobile sites. A new survey conducted by Adobe, a leader in software for the design and publishing industry, reveals great interest...
Read MoreTwo new viruses have been discovered to infiltrate systems through removable drives. USB flash drives have become indispensable to almost everyone who uses a computer. It’s a quick...
Read MoreA UPS, or uninterruptible power supply, is one of the essential components your IT system should have so you can continue working even during power interruptions. Keeping productivity...
Read MoreJump Lists are lists of recently opened items, such as files, folders, or websites, organized by the program that you used to open them. You can also pin...
Read MoreThreats to the security of your organization cannot only come from malware, hacks, and network attacks, but also in more subtle ways. One such method is called “social...
Read MoreNeed to quickly find out what day it would be 45 days from now without counting squares on a calendar? Want to know how many days until a...
Read MoreHidden IT costs can be stifling your company and you just don’t know it. It’s important to assess what those costs are and find a way to help...
Read MoreBefore you entrust your sensitive data to a “cloud” service provider, make sure you weigh the risks with the benefits. “ Cloud computing ,” largely synonymous with Internet-based...
Read MoreTo see images the way they are intended to be seen, calibrate your monitor so that what you see is what you get. Here’s how. Read more ....
Read MoreRunning an environment-friendly business may seem like too much of a hassle, but in truth, you can save money. There’s been a lot of buzz about environmental issues...
Read MoreScanners are the critical link between the non-digital and the digital world. Any picture or document can be turned into a digital format with a scanner. When looking...
Read MoreDespite the clear trend towards greater adoption of mobile devices by businesses and consumers, a new study finds that many businesses are not taking full advantage of the...
Read MoreThe continued exploit of many vulnerable applications that have been fixed by vendors for over a year highlight the need to keep software updated with the latest versions...
Read MoreMozilla implements new initiatives to ensure the security of its browser to fix the main security holes, and this brings Firefox’s latest version to 3.6.7 The Mozilla foundation,...
Read MoreWith mobile devices becoming a staple in business dealings these days, it’s high time companies enact policies for mobiles that will not only help them cut costs, but...
Read MoreBarely a month after a Google engineer disclosed a critical vulnerability in Windows XP, hackers have taken launched an attack on vulnerable machines. On June 10, a Google...
Read MoreThe recent fever over the FIFA World Cup made unsuspecting victims an easy target for malware makers, spammes, and scammers using the sport as a means to spread...
Read MoreImplementing a client-server network and maintaining it with Managed Services can help small to medium-sized businesses prevent data loss events, which lead 43 percent of such businesses to...
Read MoreAre you getting a “USB device not recognized” error for a USB mouse, keyboard, or other USB device? Already tried normal fixes, such as uninstalling and reinstalling the...
Read MoreWork no longer has to be a place your employees go at a certain time. Learn what technologies can enable your employees to get more done from any...
Read MoreClient-server networks can help employees perform 20 percent more revenue-producing tasks. For small to medium businesses that may not be able to afford a dedicated IT staff, outsourcing...
Read MoreDo you want to lock and password-protect your important folders in Windows 7 or Vista? If you have multiple accounts including one with administrator privileges in Windows 7...
Read MoreThe near ubiquity of WiFi hotspots nowadays has led to great advances in access and convenience for many. It’s also a great boon for “road warriors” who do...
Read MoreA critical vulnerability in Windows XP has been revealed that involves the Windows and Help support center, a Web-based feature providing technical support information to end users. The...
Read MoreA recent report , released by Osterman Research and sponsored by software vendor Commtouch, reports that the incidents of outbound spam is getting worse. The research firm interviewed...
Read MoreUSB flash drives have become a popular choice for people needing a convenient, portable, and cheap storage device for their data. Unfortunately, as the use of these devices...
Read MoreIt’s not uncommon for many small and medium-sized companies to use file sharing and peer-to-peer (P2P) platforms as a means to share information and data – especially when...
Read MoreManaged Services provide enterprise-level IT capabilities without a large initial capital investment for a predictable monthly fee—which can be appealing to small and medium-sized businesses such as yours....
Read MoreOf course we’ve all heard of the saying “If it ain’t broke, why fix it?” And really, to some degree, that saying holds true. When it comes to...
Read MoreWeb-worker Daily shares some useful tips on how to improve your efficiency using dual monitors with your computer. Both Mac OS and Windows support dual monitors, and you...
Read MoreBusiness impact analysis is an often misunderstood component of your business continuity plan—but it doesn’t have to be. First, let’s review business continuity planning, which is simply the...
Read MoreWant to get rid of that annoying white box that appears around your logo when you place it in PowerPoint? ZDNet’s Techguide shares a useful tip on how...
Read MoreOnline security website OneITSecurity recently interviewed Charlie Miller, second-year Pwn2Own contest champion, and he shared several interesting insights on browser security – especially with the use of Adobe’s...
Read MoreIf you travel for business, chances are you need to connect to the Internet while on the road. Here are some tips to help: Set up wireless access....
Read MoreThe average computer and Internet user manages over a dozen passwords for various websites. You probably have passwords for your computer, your company email, your personal online email...
Read MoreThere are few (if any) people who’ll tell you that technology has reached its limit. On the contrary, technology continues to grow every day, leaving information technology companies...
Read MoreThere are plenty of general tips at various websites and blogs for air travelers, but few address travelling with your laptop and gadgets in tow. The following advice...
Read MoreIndustry analyst IDC predicts that the global economic recession will have a dramatic impact on small and mid-sized companies. But that doesn’t means these companies will stop spending...
Read MoreAs networks and devices become increasingly complex, more and more things can go wrong. As a result, disaster recovery plans have also become more complex. Is yours good...
Read MoreIt seems that even the most innocuous machines in the workplace can serve as a security threat to companies. According to this report from CBS News, many office...
Read MoreYou can create a keyboard shortcut for your favorite websites using Internet Explorer. Read more http://www.computerhope.com/tips/tip1.htm
Read MoreInc.com posted five business uses for your digital frame, including using it as a presentation tool at tradeshows or as an ice breaker before a meeting. Read more...
Read MoreA paperless office is one of the simplest ways a company can minimize clutter and mess, and also help contribute to making business operations more green and environment...
Read MoreHackers are employing increasingly sophisticated techniques to scam users into downloading malicious software. For instance, today’s hackers and malware authors have begun using so-called “doorway pages” – web...
Read MoreConsider this: according to research by technology analyst group Gartner , beyond 2010 end users, not the IT department, will be responsible for 50 percent of business IT...
Read MoreViruses and other forms of malware can wreak untold havoc in your computer systems, which causes productivity loss and problems that affect the service you deliver to your...
Read MoreIf you’re like most small or medium-sized businesses, you’ve become increasingly dependent on IT—and you want your IT to provide the functionality and security that large enterprises enjoy....
Read MoreIt’s simple: Businesses that suffer data losses usually fail as a result. That’s according to a study by the Department for Trade and Industry, which found that 70...
Read MoreMoney is tight and hard to come by, and a lot of companies are looking to cut costs and sacrifice the non-essentials. For many, taking off a chunk...
Read MoreAnticipation for Apple’s iPad, the company’s entry into the nascent “ tablet PC ” market, has been building especially since it hits retail stores this April. While early...
Read MoreThe new Windows 7 taskbar allows you to dock items to the taskbar, combining the features of both the normal taskbar as well as Quick Launch. But what...
Read MoreThe single most visible change in Windows 7 is the new “dock style” taskbar, which shows icons instead of buttons, with all application windows combined within a single...
Read MoreA survey conducted by the Messaging Anti-Abuse Working Group or MAAWG reveals that a almost half of computer users in North America and Western Europe not only open...
Read MoreDo you use the the Energizer DUO USB battery charger? If so, you’ll be interested to know that the United States Computer Emergency Response Team (US-CERT) has warned...
Read MoreAs we begin to store more and more of our data on the Internet and in the “Cloud,” the threat of that data being accessed and used by...
Read MoreMcAfee posted on its blog recently news about e-mail purportedly coming from Facebook urging recipients to open an attachment to get their new password on the site. Unfortunately...
Read MoreUsers beware of ransomware : malicious software that extorts money from users in exchange for freeing the user’s computer or data. One particularly nasty version was recently discovered...
Read MoreHold on to your mobile devices: IDC predicts 20.9% growth in smartphone sales from 2009 through 2013. Symbian and Research In Motion (RIM) remain the market leaders, but...
Read MoreYou can’t have a disaster recovery plan until you first have a good backup solution. Is your backup solution good—or just good enough? The traditional backup process is...
Read MoreFinding a way to easily access recently used files, folders, and websites was annoying to some in previous versions of Windows. In Windows 7, the new Jump List...
Read MoreIt’s March again, and many hoops fans are once again in a frenzy – creating fantasy basketball drafts, watching streamed basketball games, and researching basketball trends, rumors, and...
Read MoreA cool feature in Windows 7 Media Center is the ability to listen to local FM radio. But what if you don’t have a tuner card that supports...
Read MoreIn today’s tough market environment, many small and medium businesses are turning to Managed Services. But is the up-front cost worth it? We say yes—and think you’ll agree...
Read MoreBusinesses are constantly changing. Is your disaster recovery plan changing, too? It should be. Every company can experience a business-altering event at any time: floods, explosions, accidents, computer...
Read MoreSpanish authorities report that they have arrested the masterminds behind a string of online criminal activities using the botnet dubbed Mariposa. Mariposa is the original name of a commercially...
Read MoreSaaS has several characteristics that set it apart from other services: SaaS allows the access and use of commercially available software through a remote, network, or internet connection....
Read MoreMicrosoft recently released a number of security bulletins and patches addressing vulnerabilities in Windows and Office that are of high risk to users. It’s widely believed that many...
Read MoreA malicious piece of software making the rounds of news websites this week is believed to be behind the compromise of over 75,000 systems in over 2,500 international...
Read MoreFor businesses of all types and size, managing data online is critical to the smooth operation of a website. However, incorporating data collection programs can be time consuming,...
Read MoreIf you suspect that you’ve responded to a phishing scam with personal or financial information or entered this information into a fake Web site, take these steps to...
Read MorePhishing, pronounced “fishing,” is a type of online identity theft that uses e-mail and fraudulent Web sites that are designed to steal your personal data or information such...
Read MoreThe growing reach and power of the internet has changed the way people do business, with more and more web-based services popping up. One of these is SaaS....
Read MoreMost small and medium businesses can’t afford the luxury of a qualified IT administrator, let alone an entire IT department. If you’re in this position, how do you...
Read MoreIn a report by security firm Websense , an alarming rise in the growth of malicious websites was identified in 2009 as compared to 2008 – almost 225...
Read MoreMozilla , the organization behind the popular Firefox browser disclosed that two add-ons available for download on its website were vectors for Trojans that could compromise users’ computers....
Read MoreWith the start of a new year, businesses commonly implement changes and launch new initiatives that have ramifications for your IT environment. Ignore them at your own peril....
Read MoreMuch has been said about the launch of Apple’s long awaited, new mobile device . Called the Apple iPad, the device promises to boost sales of a new...
Read MoreMorgan Stanley has just released the Mobile Internet Report , which estimates that within five years, more users will access the Internet via mobile devices than desktop PCs....
Read MoreFor many people, learning begins by understanding the basic principles that drive a certain concept. Whether in technology or science or society, the world is filled with so...
Read MoreSecurity firm Imperva recently released a warning to users of popular social networking website RockYou indicating that their accounts and passwords may have been compromised. According to the...
Read MoreEarly January, Google released a report detailing attacks on its infrastructure which it claimed to have originated from China. In the wake of its announcement, another report came...
Read MoreRealNetworks , developers of RealPlayer, a popular real-time streaming media player, recently released an advisory about vulnerabilities that when exploited could trigger remote code execution attacks. The firm...
Read MoreIMPORTANT UPDATE FOR QuickBooks Customers: Intuit is receiving reports of individuals receiving fraudulent emails from QuickBooks or QuickBooks Online. The two separate emails ask customers to either download...
Read MoreWhen you want to thank loyal customers and reconnect with friends, greeting cards offer a great way to reinforce the personal link between you and them. Using Microsoft...
Read MoreTypically, reminders are associated with tasks and deadlines. However, reminders are versatile and can be used with calendar items, e-mail messages, and contacts as well as tasks. Learn...
Read MoreWith more and more people and organizations accessing the Internet, and as the potential uses of the web grows, the way business is done is naturally evolving as...
Read MoreManaged IT services are the technology solution of choice for large businesses, but many small and medium businesses remain resistant to considering this approach. Below are five reasons...
Read MoreSmall and medium-sized companies sometimes think that disaster planning is only for larger corporations, but recent changes in technology make such planning affordable for almost all business sizes....
Read MoreThe prevailing bad weather in the United States and Europe has caused varying degrees of production delays in all sorts of industries and business. In circumstances like these,...
Read MoreYou expect your computer to work when you turn it on. The last thing you want is to waste valuable time trying to get your email running or...
Read MoreTrusteer , a security solutions vendor, recently released the results of their study which shows how successful phishing attacks are, how many users respond to phishing attacks, and...
Read MoreQuoting research from various industry analysts, Microsoft warned that users who install unlicensed or counterfeit software on their PCs are 73% more likely to suffer data loss or...
Read MoreIn Microsoft Word, you can use mail merge to create a batch of envelopes when you want to use envelopes to send a mass mailing to your address...
Read MoreA PowerPoint photo album is a presentation that you can create to display your personal or business photographs. You can add effects that include attention-grabbing slide transitions ,...
Read MoreA new report by security vendor Cenzic shares research indicating that security flaws found in Web applications continue to grow and should be a major concern for many...
Read MoreMicrosoft Office Publisher makes it easy to produce effective business cards, whether you create your own design or use one of the Publisher designs. You can use color...
Read MoreMicrosoft Office Access 2007 makes it easy to gather data from people who are located anywhere on the globe, such as members of your sales team, survey participants,...
Read MoreNew research from the Ponemom Institute and Lumension , shows that a majority of firms are struggling to secure data as users quickly adopt new and emerging technologies...
Read MoreEntrepreneur Magazine ‘s Scott Steinberg shares in his online column Top Ten reasons why Small Businesses should use Windows 7 . Among them: lower system requirements than Vista,...
Read MoreIf you are using an automated clearing house (ACH) system to manage your funds, then you had better be extra careful. The Federal Bureau of Investigation (FBI) has...
Read MoreThe National Cyber Security Alliance (NCSA) and Symantec recently released the results of a survey they did as part of National Cyber Security Awareness Month to assess the...
Read MoreIf you have decided to use Social Networking technologies for your business in your marketing, public relations, employee relations, or any other initiative, congratulations – it’s a good...
Read MoreHighly respected technology writer Walt Mossberg from the Wall Street Journal calls Windows 7, “A Windows to Help You Forget” – and with good cause. We all remember...
Read MoreThe recent release of Windows 7 has seen much more good than bad – which cannot be said for its predecessor, Windows Vista. Even in the early stages...
Read MoreIf you’re excited about upgrading to Windows 7 , you’re not alone. Reactions are coming in from people who have tried the new operating system and so far,...
Read MoreYou can customize the way that Microsoft Office Excel 2007 starts by adding switches and parameters to the startup command. For example, you can prevent the startup screen...
Read MoreWhen you use Microsoft Office PowerPoint 2007 to deliver your presentation, you can circle, underline, draw arrows, or make other marks on the slides to emphasize a point...
Read MoreHotmail, Microsoft’s free online email service, finds itself in hot water when 10,000 email accounts usernames and passwords were recently discovered posted in a code-sharing website. BBC News...
Read MoreTwitter , the microblogging service used by CNN , Oprah and none other than President Obama seems to have taken the world by storm, and is fast becoming...
Read MoreWith many people using the same computers, printers, copiers, and telephones every day, there are a myriad of diseases that can be caught at work if you’re not...
Read MoreThese days it seems like everybody is talking about “social networking” and using websites such as MySpace , Facebook , and Twitter . But exactly what is social...
Read MoreSocial Networking websites are usually associated with consumer services such as MySpace and Facebook . But did you know that there are literally dozens of social networking websites...
Read MoreFrom the heavyset computing devices of Charles Babbage to today’s simple novelty items, electronic devices and gadgets have become smaller, more functional, and more integrated into our daily...
Read MoreA recently released a report entitled “Voice of IT: State of SMB IT”, detailing purchasing, technology usage, and IT staffing trends among small and medium businesses worldwide. The report...
Read MoreIn a previous post, we pointed out how just browsing the web these days can possibly infect your PC with malware . To show how dangerous surfing can...
Read MoreA recent study by the Kelsey Group reveals that more small and midsized businesses are using digital media, specially the Internet, to promote or advertise their business. Their...
Read MoreOrganized criminals believed to be based in Eastern Europe are robbing small to midsized US businesses of millions of dollars via an elaborate scheme aided by malicious software...
Read MoreAs a result of the past year’s economic climate, many small and medium-size businesses have increased their efforts to mitigate risks and lower costs—and more and more are...
Read MoreVirtualization is generating a lot of buzz in IT circles these days because it promises to dramatically change the way many companies manage and operate their IT infrastructure....
Read MoreCarpal tunnel syndrome and eyestrain are two of the most common conditions that affect habitual computer users. Whether or not these conditions pose serious health risks remains a...
Read MoreAnother reason to keep your computer malware free: cyber-pirates raided several businesses as well as a school in recent attacks through the Automated Clearing House (ACH) Network. The...
Read MoreEntrepreneur magazine columnist Gail Goodman offers an insightful look into email marketing and its relevance in today’s social network marketing -crazy world. She argues that despite the rise...
Read MoreA new report by PandaLabs , Panda Security’ s malware analysis and detection laboratory, examines the proliferation of so-called “rogueware” – malicious software that attempts to convince people...
Read MoreMicrosoft recently announced the availability of the Release Candidate for Windows XP Mode . According to Microsoft, this release was specifically designed to ease the migration path for...
Read MoreMicrosoft recently announced that Windows 7 will include a feature to allow instant upgrades from lower editions of Windows 7 to a higher edition (i.e., from Starter to...
Read MoreInformation Week has posted a helpful guide to assist those planning to upgrade to the upcoming release of Microsoft Windows 7 on their existing Windows XP machine. Long...
Read MoreFrom annoying to destructive, malware is a bane to any computer system and the person who uses it. The benevolent Wikipedia defines malware (short for malicious software) as:...
Read MoreIf you enable your employees to work where and when they like, at any hour of any day, you’ll likely see big gains in productivity. With traditional network...
Read MoreAt the recently concluded Microsoft World Wide Partners Conference , the company gave partners a preview of upcoming features in Microsoft Office 2010 that could be very useful...
Read MoreNew research suggests that small and midsized businesses are struggling to keep up with securing their IT applications and infrastructure. The IT Effectiveness Index report , or ITEI,...
Read MoreThe internet makes a great number of tasks more convenient for many people, especially in the area of communication. The power of the internet allows millions of people...
Read MoreWhile software companies have made significant progress in protecting customers from malicious online threats, these threats continue to evolve, and now a new player has entered the game:...
Read MoreThe web is indeed becoming a dangerous place. These days, your PC could become infected with malware or vulnerable to a hacker attack just by innocently browsing a...
Read MoreFor many small and medium-sized businesses, the cost of maintaining an old PC may be more expensive than upgrading to a new one. This insight comes from a...
Read MoreMicrosoft has finally announced the pricing for the much anticipated new version of its flagship product, Microsoft Windows , expected to go on sale this October. Users will...
Read MoreOutlook is surely one of Microsoft’s most popular products, widely recognized as a standard application alongside Word, Excel, and Powerpoint. Bundled inside Microsoft Office, Outlook is the personal...
Read MoreIn today’s challenging economic times, many small businesses like yours are reluctant to spend money. However, a modest investment in network maintenance can ultimately improve your profitability and...
Read MoreData breaches are costing companies more than ever, according to a recent study—and smaller companies may be most at risk. Data losses, which can result from theft or...
Read MoreIs it time for you to consider a server for your business? This question was raised recently by Rhonda Abrams, a writer for USA TODAY’s Small Business section....
Read MoreLast July 4th and 5th, a massive denial-of-service attack was launched against several government and commercial websites in the United States and South Korea. According to security researchers,...
Read MoreExcited about Windows 7 but unsure if you want to replace your existing Vista installation? Worried about potential compatibility and driver problems with the Windows 7 beta or...
Read MoreMarket research organization Techaisle recently released a study forecasting that SMBs worldwide will purchase 1.1 million Netbooks in 2009, jumping to 3.5 million units in 2010. Between 22...
Read MoreWhen most people want to purchase a new computer or upgrade their current one, they focus on finding a CPU with the quickest speed, the most computing cores,...
Read MoreSurprise, surprise! According to Forrester Research , an analyst firm, small businesses buy and use software differently than their larger brethren. More than 2,200 IT executives and technology...
Read MoreNew research from security firm Secunia reveals that the average PC user has over a dozen insecure applications on his or her computer. They found that the typical...
Read MorePDF stands for Portable Document Format , a file format that originated in print publishing as a tool for proofing print jobs before sending them to the printer....
Read MoreAs if the scare from the Swine Flu virus were not enough, some opportunistic and malicious hackers have started spreading a computer virus with emails of the same...
Read MoreCyber-Ark Software, a security solutions company, recently released a survey showing that as much as 35 percent of people within an organization (that’s one out of three) admit...
Read MoreWhat are the key technology lessons that small and mid-sized businesses can learn from large enterprises? Be proactive. Be prepared. Take security concerns seriously. Always watch for ways...
Read MoreRumors abound that we may soon see Microsoft’s Office suite on mobile devices. Some people are speculating that it may even be made available to the (gasp!) Apple...
Read MoreWith the continuous proliferation of data and its increasing importance to business, it has become critical to implement measures to safeguard it. One such measure is to make...
Read MoreSmall businesses will get a helping hand with some key expenses under President Obama’s $787 billion stimulus plan, signed into law on February 17. Around $282 billion of...
Read MoreIn today’s tough economic environment, converting your most promising prospects into customers and your current customers into loyal patrons is more important than ever. Whether your business is...
Read MoreMicrosoft Windows 7 will be in stores October 22, but surprisingly few details of its features have been released. Thankfully, Ed Bott, a ZDNet blogger, researched it for...
Read MoreGoogle announced the release of a new Local Business Center feature called Search Dashboard that promises to help small businesses gain insight into how visitors came across their...
Read MoreWhile the internet is a vast resource for all sorts of information, data, and other useful thingamajigs, there are aspects of it that aren’t so desirable. Viruses, for...
Read MoreDo you frequently struggle with creating PDF documents, sending large files through email, and converting various file types from one to another? If so, you may have found...
Read MoreLast April 14, Microsoft officially announced the end of mainstream support for Windows XP , seven years after XP originally shipped. Non-security patches, fixes, and updates are no longer...
Read MoreResearch recently released by antivirus vendors Mcafee and Panda suggest that searching for certain key words on Internet search engines can prove dangerous.Hackers and malware authors have become...
Read MoreA new study, “ Understanding Growth Priorities of Small and Medium-sized Businesses ” conducted by the Economist Intelligence Unit and sponsored by services company Verio, finds that 83...
Read MoreApparently, the well known adage “All work and no play make Johnny a dull boy” isn’t just some excuse to be laid back and take a break from...
Read MoreTech-savvy criminals have thought of with a new way of scamming us out of our money. In a twist to “ phishing ” (when spoofed websites are used...
Read MoreSecurity company Websense released a survey of of 1,300 IT professionals worldwide revealing that although social media or the use of “Web 2.0″ technologies such as blogs ,...
Read MoreVoice over Internet Protocol (VoIP), technology that lets you make and receive phone calls over the Internet, may have started out as a novelty, but it’s quickly becoming...
Read More3 Reasons 2 Screens are Better than 1 Increasing your employees’ online workspace by expanding it across two or more monitors can significantly improve productivity with minimal cost...
Read MoreIt’s All in the ‘How’ Have you ever wondered how to fix a leaking pipe or a broken light? Or how to check your car’s coolant or radiator...
Read MoreAre you avoiding instant messaging (IM) for fear that it will distract your employees and cut productivity? In fact, the opposite may be true. What is IM? IM...
Read MoreThese days there’s a lot of buzz about “ going green ” – helping preserve the environment, conserving energy, and looking for sustainable ways to grow the economy....
Read MoreLast May 14th, reports indicated that hackers had launched a phising attack on Facebook ‘s 200 million users, successfully stealing passwords from some. The hackers set up websites...
Read MoreWhile everyone is worried about security threats outside the company’s firewall such as hackers, viruses, and worms, research suggests that the greatest risk may come from none other...
Read MoreInstant Messaging , or IM, can be a boon for any business because it saves time, improves efficiency, and even enables greater employee/customer intimacy. IM allows real-time communication...
Read MoreResearch conducted by SIS International Research and sponsored by Siemens found that small and midsized businesses (SMBs) with 100 employees could be leaking a staggering $524,569 annually as...
Read MoreMicrosoft recently announced the release of the newest service pack to Microsoft Office 2007 , and has finished work on the second service pack update to Windows Vista...
Read MoreThe past couple of weeks, a new malicious and particularly virulent worm known as Downadup, also more popularly known as Conficker has started to infect millions of PCs....
Read MoreLooking for a website or online resource for Security Tips and Best Practices? Check out the Federal Trade Commission ‘s (FTC) OnGuardOnline program , which the FTC began...
Read MoreSocial Media such as Blogs, Micro-blogs, Wikis, and Social Networks are not only helping many people communicate and connect, but are also powerful tools for business as well....
Read MoreApril fool’s day came and went, but so far the much feared attack from Conflicker never materialized, leaving security researchers to ponder what’s next for the notorious Internet...
Read MoreNever before have startup entrepreneurs and small business owners had access to so much marketing advice and tools as we have today on the Web. There are hundreds...
Read MorePC World posts a nice overview of the highly infectious Conflicker Worm. The Worm is dangerous as it uses several methods of attack. Once one computer in a...
Read MoreJanet Attard of The Business Know-How Blog posts 18 tips for small businesses considering outsourcing. She offers insight on how to get the best possible results from outsourced...
Read MoreMicrosoft announced that is has granted system builders a “flexible” delivery date of Windows XP licenses to customers beyond the official phase-out deadline of January 31, 2009. PC...
Read MoreLately, we have been hearing about how quickly the Conficker Worm is spreading. News sources have pegged the number of infections in the neighborhood of 3.5 million computers....
Read MoreIn 2009, IT experts predict more malware and other attacks on company networks coming from mobile devices, social networks, and faster Internet connections, among other trends. IT experts...
Read MoreWhether the economy is up or down, no matter what is happening in the world, most small business owner’s work hard anyway. It’s never been easy to start...
Read MoreWe all want to minimize costs – both planned and unexpected – but not at the expense of keeping systems and essential equipment running smoothly. Small businesses without...
Read MoreOnline fax services are becoming extremely popular with business owners. There are several reasons why Internet or online faxing has found favor with the business sector. Mainly because...
Read MoreBrand building is indeed a journey. Branding is all about how your product or service is perceived by customers and potential customers. A brand marketer attempts to manipulate...
Read MoreOne of the key characteristics of Web 2.0 is participation, collaboration and moderation through the use of web applications. Web 2.0 sites derive their power from the human...
Read MoreFor the past few months I’ve been using a variety of wireless, blue tooth headsets, with my cell phone. The latest head set I’m using does not have...
Read MoreAs a kid I used to write messages with lemon juice and when the juice dried I had a secret message (or so I thought) that was viewable...
Read MoreWhen an economic downturn starts to hurt, small businesses often hunker down and cut costs. But new technology solutions may be necessary for survival and growth—and they may...
Read MoreWhen you have to lay off staff, software-as-a-service can often make up the difference, especially in sales and marketing. Every business wants a hot niche, and Starr Tincup...
Read MoreWhen you first opened your Smartphone and took it right from the fresh, “new smelling” box (or from the plastic sandwich bag from the friend you bought it...
Read MoreMore business people are taking to the road these days, armed with all the tools they need to do their work — PDAs, laptops, etc. So it pays...
Read MoreWhen the toner runs out of the printer in your office do you run to change it or do you cringe, shaking at your desk, just hoping some...
Read MoreThere comes a point when gadgets detract from meetings. Or does there? Companies are coming up with different strategies to manage technology in the meeting room. Read more...
Read MoreBusinesses need to use the economic crisis as a time to reassess their IT needs and options. Server virtualization, consolidation, and energy costs are a good place to...
Read MoreWhen an economic downturn starts to hurt, small businesses often hunker down and cut costs. But new technology solutions may be necessary for survival and growth—and they may...
Read MoreWhen an economic downturn starts to hurt, small businesses often hunker down and cut costs. But new technology solutions may be necessary for survival and growth—and they may...
Read MoreWhile the internet essentially puts the entire world right outside your storefront door, there are challenges to selling abroad – from shipping to understanding local customs and preferences....
Read MoreWelcome to microblogging, a new form of Internet communication that has interesting business possibilities. Twitter started as a personal service, where members answered the question “What are you...
Read MoreWhether it’s to clinch a sale, show off a new product or discuss a potential acquisition, the digital projector is major part of everyday corporate work. Welcome to...
Read MoreWhat will the financial crisis mean to your business’ IT budget? Will there be pressure to make existing IT systems go farther? On the other hand, is this...
Read MoreIn 2009, have a “tech audit” with your consultant and let her review your day to day business processes and see how technology can help. Read the story...
Read MoreWhat are the new technologies that stand to change the way you do business in 2009 and beyond? Here are at 10 to consider. Read the story on...
Read MoreWireless networks have moved to the small business arena, helping offices spread Internet connectivity and mobility at a low cost, but bringing security concerns. Unauthorized access points can...
Read MoreA variety of software and services — from Lojack to GadgetTrak — are designed to help recover a lost or stolen notebook computer. These products have become more...
Read MoreNotebook computer vendors are now more aggressively pushing to have you buy a mobile wireless card that’s built into your computer. Nothing to lose, nothing to break –...
Read MoreYou’ve probably had this experience: Your printer tells you it’s time to change the cartridge, but you dismiss the message and keep printing. Days or weeks later, you’re...
Read MoreAs a busy small business owner, you may not have had time to learn much about social networks. Or, you may think that social networking is just a...
Read MoreA one-dollar reduction in the after-tax cost of research and development creates an additional dollar of new spending in the short term and two dollars of additional spending...
Read MoreIt’s almost impossible to find a company today that does not have a website that provides at least information about the company and ways to make contact. This...
Read MoreReading this article will help you understand just what an Intranet is and how it can help your company be more organized and your teams more productive. And...
Read MoreReading this article will help you understand the pros and cons of internal IT Staff or external IT Consultants. In today’s world you’d be hard pressed to find...
Read MoreReading this article will help you take control of email by reducing unwanted email and making your email time more productive. If you’ve never experienced the feeling of...
Read MoreWhy you should care… Email is perhaps the most important productivity tool available – yet its potential as a time waster is well known. It’s essential that you...
Read MoreReading this article will give you an overview of tools and technologies that will help you and your teams collaborate effectively and productively. Collaboration and teamwork can make...
Read MoreSimple Steps Businesses Can Take to Protect Themselves from Cyber Crime “When the World Wide Web launched almost 20 years ago, it generated a lot of buzz about...
Read More“There are some steps that small business owners should take today that will help them tomorrow when it comes to understanding and deploying technology. It seems so obvious...
Read More“Microsoft has announced new server software that it said provides small and medium businesses with enterprise-quality capabilities while helping them to save money, increase productivity and grow their...
Read More“Lower costs and ease of use mean companies of any size can create their own intranets. Here’s how to get the most from this technology. Seven years ago,...
Read MoreMicrosoft Dynamics is committed to helping credit-approved customers gain access to capital and invest in their businesses even in uncertain times. REDMOND, Wash. — Nov. 13, 2008 —...
Read MoreSolutions designed to help small and midsize businesses save money and compete in a global marketplace. REDMOND, Wash. — Nov. 12, 2008 — As part of Microsoft Corp.’s...
Read More